Real-World Examples of Compliance in Healthcare
- Home
- Healthcare Compliance Software
- Real-World Examples of Compliance in Healthcare
Learning about rules is one thing. Seeing them in action is another. This article is about how something is accomplished. We will look at real examples of compliance in healthcare, from daily office habits to multi-million dollar legal cases. These cases show how following the rules protects patients and keeps organizations running.
They also show what happens when things go wrong. Let’s make sense of compliance by looking at the real world.
Why Is Healthcare Compliance Important?
- First, it is about people. Rules for patient privacy, clean equipment, and proper medicine dosing exist to prevent harm. Compliance builds the trust that lets a patient share their most personal information with a doctor. Without that trust, the whole system falls apart.
- Second, it protects the system’s integrity. Laws against fraud and kickbacks make sure money from Medicare and insurance is spent on actual patient care. This keeps costs down for everyone and makes sure resources go where they are needed most.
- Finally, it is a matter of survival for the organization. A major compliance failure can shut down a hospital or clinic. The financial penalties are massive. The damage to reputation can last for years, driving away patients and skilled staff. In short, compliance is not red tape. It is the framework for safe, ethical, and sustainable care.
Ready to Simplify HIPAA Compliance?
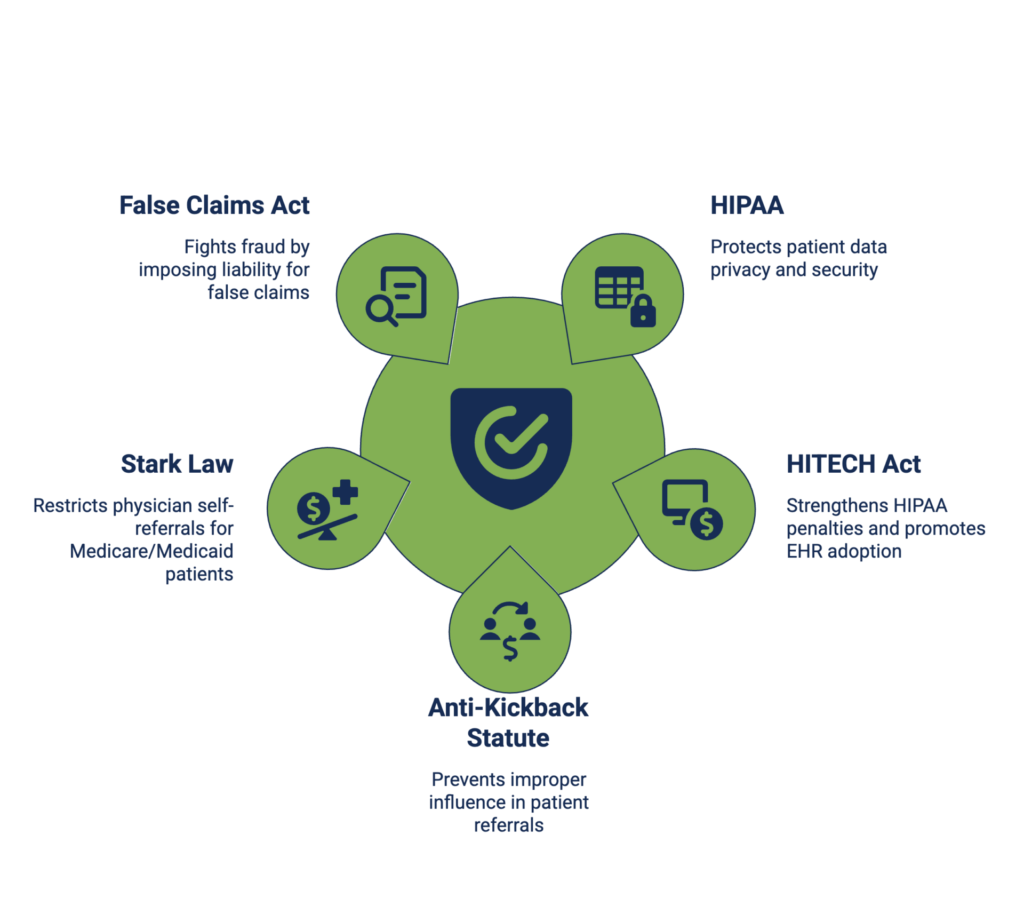
What Are the Main Healthcare Compliance Laws?
Healthcare operates under a web of rules. Five federal laws form the core of this legal framework. Understanding these is not just for lawyers. It is for every leader and manager who makes decisions about patients, payments, or partnerships.
HIPAA (Health Insurance Portability and Accountability Act)
HIPAA is the primary law for patient data privacy and security. Its Privacy Rule controls how information is used and shared. Its Security Rule requires specific technical, physical, and administrative protections for electronic records. Its Breach Notification Rule dictates what to do if data is exposed.
HITECH Act
This law gave HIPAA more teeth. It increased the penalties for violations and made breach reporting more transparent. It also promoted the adoption of electronic health records, which created new data security challenges and requirements.
Anti-Kickback Statute
This law is about improper influence. It makes it illegal to knowingly offer, pay, solicit, or receive anything of value to reward patient referrals for services paid by federal healthcare programs. Even if the care is good, the illegal referral arrangement breaks the law.
Stark Law (Physician Self-Referral Law)
This law is more specific than the Anti-Kickback Statute. It stops a doctor from referring Medicare/Medicaid patients for certain “designated health services” (e.g., lab tests or physical therapy) to an entity with which the doctor or an immediate family member has a financial relationship, unless an exception applies.
False Claims Act (FCA)
This is the government’s primary tool for fighting fraud. It imposes liability on anyone who knowingly submits a false claim for payment to the government. In healthcare, this includes billing for services not rendered, “upcoding” to get a higher payment, or billing for medically unnecessary services.
Healthcare Compliance Examples in Daily Operations
These examples of compliance in healthcare show how organizations build rules into their routine to keep patients safe and stay within the law.
Data Security Example
Protecting patient data from unauthorized access is critical to maintaining confidentiality and trust. A simple healthcare compliance example involves the management of sensitive patient records in electronic systems.
The Scenario
An outpatient clinic implements a policy where every computer in patient rooms automatically locks after five minutes of inactivity. The clinic also requires that any portable devices, like laptops and tablets, have full-disk encryption enabled before being issued to staff. Additionally, all staff must complete a digital training module on data security best practices once every quarter.
The Compliance Link
This policy aligns directly with the HIPAA Security Rule, which mandates that healthcare organizations implement technical safeguards to protect ePHI. The automatic lock feature ensures that patient information is protected from unauthorized access if a staff member steps away from a workstation. Full-disk encryption secures patient data in the event of a lost or stolen device.
Patient Safety Example
Keeping patients safe from harm is the most important goal. A simple healthcare compliance example is a standardized process for giving high-risk medication.
The Scenario
The hospital’s procedure statues, before a nurse gives a dose of insulin or a powerful blood thinner, a second nurse must double-check three things: the right patient, the right drug, and the right dose. Both nurses must sign a digital log.
The Compliance Link
This rule follows standards set by groups such as The Joint Commission and federal rules for hospital participation. It directly stops dangerous medication errors. It creates a clear record proving the organization takes safety seriously. This is compliance in action, turning a written standard into a lifesaving habit.
Patient Privacy Example
The HIPAA Privacy Rule is about respect in everyday moments. A common example of compliance in healthcare happens at the front desk.
The Scenario
A check-in clerk is trained to lower their voice when asking for a patient’s date of birth. They are taught to escort patients to a private room, not the open desk, to discuss a bill or a sensitive test result. Paper schedules at the desk do not use full patient names.
The Compliance Link
This applies the Privacy Rule’s “Minimum Necessary” standard and safeguards requirement. It protects information from being overheard or seen by others in the waiting room. These small, consistent actions show staff understand that privacy is part of their job, not just a rule in a manual.
Data Security Example
Protecting electronic records requires both smart policies and smart technology. A key healthcare compliance example involves basic computer settings.
The Scenario
An outpatient clinic configures all computers in exam rooms and nursing stations to automatically lock after five minutes of inactivity. To unlock it, the user must type their password again. Furthermore, the clinic’s policy states that any laptop or tablet that can leave the building must have full-disk encryption turned on before it is issued to an employee.
The Compliance Link
This directly fulfills the requirements of the HIPAA Security Rule. Automatic log-offs are a “technical safeguard” to prevent unauthorized access if a staff member walks away. Encryption is a critical measure to protect data if a device is lost or stolen. These are clear, enforceable actions that secure patient data around the clock.
Credentialing & HR Compliance Example
Making sure every provider is qualified is a major legal duty. This process, called credentialing, is a fundamental example of compliance in healthcare.
The Scenario
Before a new surgeon can operate at a hospital, the medical staff office must complete a strict checklist. They verify the doctor’s medical license, education, and training history. They check references from past jobs and search a national database for any history of malpractice or disciplinary actions. All these verification steps are documented in a permanent file.
The Compliance Link
This meets strict standards from accreditors like The Joint Commission. It also fulfills the organization’s legal “duty of care” to its patients. By having a rigorous, documented process, the hospital proves it took reasonable steps to ensure its providers are competent. This protects patients and reduces the organization’s legal risk.
Physician Compliance Example
Doctors face unique rules about their financial relationships. Clear guidance here prevents big problems.
The Scenario
A large medical group gives its physicians an annual training session. The training explains the rules about gifts from drug companies. It provides a simple form for doctors to report any meal, trip, or payment they receive from any medical vendor over $25. The practice’s compliance officer reviews these forms.
The Compliance Link
This proactively manages risks under laws like the Anti-Kickback Statute. It helps prevent even the appearance that a doctor’s treatment decisions could be influenced by a gift. It also prepares the organization for transparency under the Sunshine Act, which requires public reporting of certain payments. This keeps the physician’s focus on the patient, not on a vendor’s incentive.
Read our guide on how to be compliant in 2026.
Five Examples of Non-Healthcare Compliance
Here are five recent cases where healthcare organizations broke the healthcare compliance rules and paid the price. We’ll look at what went wrong in each one and, most importantly, what practical steps you can take to protect your own organization.
Concentra Inc. HIPAA Right of Access Violation (2025)
Concentra Inc., a major national provider of occupational health services, became the subject of a federal investigation following a patient complaint. The patient sought a copy of his own medical and billing records from a Concentra facility in Arizona.
The Core Failure
Despite six separate requests from the patient over a year-long period, Concentra failed to provide the records. Internal communication breakdowns between the clinic and the central billing office led to extreme delays. The records were finally supplied in paper form more than 13 months after the initial request, violating the HIPAA requirement for provision within 30 days. The Office for Civil Rights determined the company did not have an effective, reliable process for handling patient access requests.
Resolution and Penalty
Concentra disputed the OCR’s findings but chose to settle before a formal hearing. The company agreed to pay a $112,500 civil monetary penalty to resolve the alleged violation of the HIPAA Right of Access provision.
Actionable Insights
This penalty serves as a critical operational warning. For executives and compliance officers, the lesson is unambiguous. Your patient records request process is a compliance liability until proven otherwise. You must audit this workflow end-to-end.
Ensure requests are routed correctly, tracked systematically, and fulfilled promptly every single time. Do not allow internal handoffs or billing disputes to create a barrier between a patient and their legal right to information. Implement a tracking system and conduct regular tests to guarantee your process works within the 30-day window. This is a fundamental duty, not an administrative courtesy.
Specialty Surgery Center of Central New York HIPAA Violation (2025)
Specialty Surgery Center of Central New York, a single-facility ambulatory surgery center, reported a data breach to federal regulators in October 2021. The breach involved a ransomware attack that compromised the protected health information of nearly 25,000 patients.
The Core Failure
Federal investigators discovered two critical, interconnected lapses. First, the surgery center had never conducted the mandatory Security Risk Analysis required by the HIPAA Security Rule. This foundational assessment, which identifies system weaknesses, was absent. Second, after discovering the ransomware attack in March 2021, the center failed to notify affected patients and the Department of Health and Human Services within the required 60-day window. Notifications were delayed by more than six months.
Resolution and Penalty
The center settled with the Office for Civil Rights, agreeing to a $250,000 penalty. As part of the settlement, it must also adopt a strict, multi-year corrective action plan. This plan mandates the completion of a risk analysis, the implementation of a risk management strategy, and comprehensive policy and workforce training reforms.
Actionable Insights
This case presents a clear before-and-after picture of cybersecurity failure. A risk analysis is never an optional IT project. It is your essential map of digital vulnerabilities. Operating without one is an open invitation to attackers.
A breach response plan is useless if it sits on a shelf. You must test and practice it. Leadership must verify that both a current risk analysis and a functional breach notification protocol are in place. The time to prepare is before a hacker provides a risk assessment for you.
Comstar, LLC HIPAA Security Rule Violation (2025)
Comstar, LLC, a Massachusetts-based company providing billing and collection services to ambulance providers, reported a significant ransomware attack to federal regulators in May 2022. The breach impacted protected health information for hundreds of thousands of individuals across its client base.
The Core Failure
An investigation by the Office for Civil Rights uncovered a fundamental security gap. Despite handling sensitive data for over 70 healthcare clients, Comstar had not performed a comprehensive, organization-wide Security Risk Analysis. By skipping this critical step, the company missed its chance to identify and fix weaknesses. This left its entire network exposed.
Resolution and Penalty
To resolve the violation, Comstar agreed to a $75,000 financial penalty. The settlement also includes a two-year corrective action plan. This mandate requires Comstar to finally conduct a proper risk analysis, create and execute a risk management strategy, and overhaul its workforce training and policies.
Actionable Insights
This case makes a painful but clear point. An ounce of prevention is worth a pound of cure. For any business associate or covered entity, a formal, documented risk analysis is your primary defense.
If you handle patient data and have not completed this assessment, you are operating on borrowed time. Leadership must treat this analysis as a non-negotiable, recurring project. The financial and operational cost of a reactive penalty and forced remediation far exceeds the investment in proactive security groundwork.
PIH Health HIPAA Violation (2025)
PIH Health, a California-based healthcare network, fell victim to a targeted phishing campaign in June 2019. Hackers gained access to 45 employee email accounts over ten days, compromising the sensitive health and personal data of nearly 190,000 patients.
The Core Failure
The incident exposed multiple, cascading failures in the organization’s compliance program. First, PIH Health had not conducted a required Security Risk Analysis, leaving its systems unprepared for common cyber threats.
When the breach was discovered, the organization’s response was fatally slow. It took seven months to report the incident to federal regulators, far exceeding the 60-day legal deadline. This delay also meant patients waited months to be notified that their most private information had been stolen.
Resolution and Penalty
PIH Health agreed to settle with the Office for Civil Rights for a $600,000 penalty. The settlement includes a mandatory two-year corrective action plan, which requires the network to perform a risk analysis, implement a risk management strategy, and overhaul its policies and workforce training.
Actionable Insights
This case demonstrates that in cybersecurity, you are only as strong as your weakest link. A single phishing email can unlock a door to catastrophic data loss if foundational safeguards are missing.
For leadership, the directive is twofold. You must implement the technical and training controls to make phishing attempts less likely to succeed. And you must have a breach response plan that is tested and ready to execute within the 60-day window. A delayed response turns a security incident into a major compliance violation. This compounds reputational damage with heavy fines. Proactive defense and a rehearsed response plan are non-negotiable.
Health Fitness Corporation HIPAA Violation (2025)
Health Fitness Corporation is an Illinois-based wellness plan provider serving clients nationally. It reported multiple data breaches to federal regulators over a three month period. The incidents involved protected health information being exposed on the internet due to a server misconfiguration.
The Core Failure
The Office for Civil Rights determined the root cause was a prolonged, systemic failure to meet a foundational requirement. Health Fitness Corporation did not perform a comprehensive Security Risk Analysis for nearly a decade. From the time the data was first exposed in 2015 until January 2024. Without this mandatory assessment, the company operated in the dark, unaware of critical vulnerabilities in its systems. This left sensitive patient data exposed and searchable online for years before the issue was finally identified and corrected.
Resolution and Penalty
To resolve the alleged violations, Health Fitness Corporation agreed to a $227,816 penalty and a corrective action plan. The company will be monitored for two years and must now conduct annual risk analyses, implement a formal risk management plan, and update its policies and workforce training procedures.
Actionable Insights
This enforcement action highlights a huge compliance misconception: that business associates face lower scrutiny than hospitals or clinics.
The penalty confirms that any entity handling protected health information is held to the same Security Rule standards. For leaders of vendor organizations, the message is clear. Your risk analysis is not a one-time project for your initial audit. It is a living process that must be repeated annually and immediately following any significant change in your technology or operations. Treating this requirement as a static checkbox, rather than an ongoing discipline, creates a ticking clock on a future data exposure and a guaranteed regulatory penalty.
Key Elements of an Effective Healthcare Compliance Program
After seeing the examples and the penalties, a question remains. What does an organization actually need to do? How do you build a system that creates good habits and stops bad outcomes? The U.S. government provides a clear answer.
The Department of Health and Human Services, through its Office of Inspector General (OIG), defines seven key parts of an effective program. These are not suggestions.
- Written Policies and a Code of Conduct
This is your foundation. You need clear, simple documents that explain the rules. A central “Code of Conduct” should state your organization’s ethical promises. Department-specific manuals should give staff step-by-step instructions for their daily work, like how to handle a patient record request or submit an accurate bill.
- A Designated Leader and a Committee
Someone must be in charge. A Compliance Officer needs the authority and resources to run the program. A committee with members from clinical, financial, and administrative areas provides oversight. This makes sure the whole organization is involved and accountable.
- Effective Education and Training
You cannot assume people know the rules. Training must be ongoing, easy to understand, and specific to a person’s job. A biller needs different training than a nurse. Annual lectures are not enough. Use regular, engaging updates that explain both what to do and why it matters.
- Open Lines of Communication
Staff must feel safe to ask questions or report a concern without fear of punishment. You need confidential ways to report problems, like a hotline. A strict non-retaliation policy is essential. If people are scared to speak up, small problems can turn into disasters.
- Internal Monitoring and Auditing
Do not wait for the government to check your work. You must check it yourself. This means regular internal audits of high-risk areas like billing and patient privacy. Conduct a formal Security Risk Analysis every year to find your technology weak spots. Finding your own mistakes first is the smartest move.
- Consistent Discipline
The rules must apply to everyone, from the front desk to the CEO. There must be clear, fair consequences for breaking policies. This shows the organization is serious. Without it, your written policies are just words on paper.
- Prompt Corrective Action
When you find a problem, you must fix it properly. This means looking for the root cause and changing the process so it cannot happen again. It is not enough to just tell one person to stop. You have to improve the system.
A program with these seven elements does more than avoid fines. It builds a culture where doing the right thing is the normal way to work. It turns the examples of compliance in healthcare from isolated actions into a connected, reliable system.
The Role of Technology in Modern Healthcare Compliance
Managing compliance with paper, spreadsheets, and memory is a recipe for failure. The volume of rules and the need for perfect proof are simply too great. This is where technology steps in. HIPAA compliance software is not just a helper. It is the essential tool that makes a consistent, defensible compliance program possible.
The best compliance software acts as a central command center. It replaces scattered files and sticky notes with one organized system. In this system, you can store the latest version of every policy and track exactly which employee read it. You can assign mandatory training courses and get automatic alerts when someone’s certification is about to expire. When an incident occurs, like a potential privacy breach, the software provides a structured way to log it, investigate, and document the resolution.
This technology also enables the proactive work that prevents crises. Built-in tools can guide your team through the annual Security Risk Analysis required by HIPAA, turning findings into a tracked to-do list. Audit management modules help you gather and organize evidence, so preparing for a government inspection is a controlled process, not a panic. Some systems can even monitor your network for unusual activity, like a staff member accessing an abnormal number of patient records, which could signal a problem.
In short, technology takes the principles from the seven-element compliance program and makes them operational. It provides the structure to follow through. It turns the intention of compliance into measurable, reportable action.
Maintain Compliance in Healthcare With ComplyAssistant
For organizations looking to move from theory to practice, a dedicated platform is the solution. ComplyAssistant is built specifically to manage the complex reality of healthcare regulatory compliance.
The platform serves as the single source of truth for your entire program. It brings together the disconnected pieces into one secure, organized system. That includes policy manuals, training records, risk assessments, vendor contracts, and audit evidence. This eliminates the dangerous gaps and errors that happen when using a mix of spreadsheets, emails, and file cabinets.
ComplyAssistant provides the structure needed at any scale. A large hospital system uses it to get a unified, real-time view of compliance status across every facility and department. A small clinic uses it to gain the framework of a complete program without needing to hire a large administrative team. The platform automates critical workflows, like sending reminders for policy reviews and training deadlines, and maintains a clear audit trail for every action. This ensures that when an auditor or investigator asks a question, you have a confident, timely answer.
With a system like this, managing compliance shifts from being a constant source of stress to being a controlled, proactive part of operations.
Frequently Asked Questions
What are examples of compliance in healthcare for nursing homes?
Main healthcare compliance examples in nursing homes include implementing strict fall-prevention programs, maintaining detailed care plans for each resident, and conducting mandatory staff training on preventing elder abuse. These actions directly fulfill state licensing requirements and federal regulations from the Centers for Medicare & Medicaid Services (CMS).
What are specific healthcare compliance examples for pharmacy drug control?
A fundamental example of compliance in healthcare in any pharmacy is using an automated dispensing system for controlled substances. This system requires biometric login and creates an unchangeable electronic log for every dose accessed. This process complies with Drug Enforcement Administration (DEA) regulations to prevent drug diversion and provides a perfect audit trail.
What is example of compliance in healthcare for medical waste?
The proper segregation and disposal of hazardous waste. Staff are trained to place used sharps in red, puncture-proof containers and chemotherapy waste in yellow containers. Using a licensed medical waste hauler with a documented chain-of-custody form complies with OSHA and Environmental Protection Agency (EPA) rules.
What are healthcare compliance examples for a medical device manufacturer?
Healthcare compliance examples for manufacturers are found in FDA processes. They must maintain a complete Design History File (DHF) documenting every stage of a device’s creation and have a system for post-market surveillance to track performance and report any injuries or malfunctions, as required by law.
